𝐓𝐡𝐞 𝐈𝐦𝐩𝐨𝐫𝐭𝐚𝐧𝐜𝐞 𝐨𝐟 𝐂𝐲𝐛𝐞𝐫 𝐃𝐞𝐟𝐞𝐧𝐬𝐞
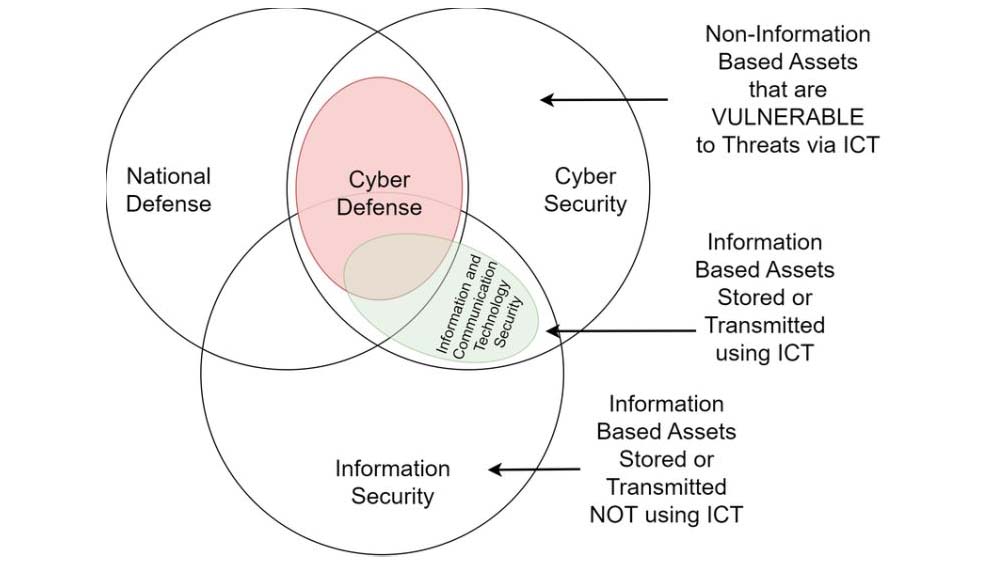
Cyber defense refers to the practice of protecting computer systems, networks, and data from digital attacks, unauthorized access, and other cyber threats. It involves implementing various strategies, technologies, and processes to safeguard digital assets, prevent breaches, detect intrusions, and respond effectively to cyber incidents.
𝐃𝐨𝐰𝐧𝐥𝐨𝐚𝐝 𝐒𝐚𝐦𝐩𝐥𝐞 𝐑𝐞𝐩𝐨𝐫𝐭: https://lnkd.in/gwjwCzaT
𝐅𝐢𝐫𝐞𝐰𝐚𝐥𝐥𝐬 𝐚𝐧𝐝 𝐈𝐧𝐭𝐫𝐮𝐬𝐢𝐨𝐧 𝐃𝐞𝐭𝐞𝐜𝐭𝐢𝐨𝐧 𝐒𝐲𝐬𝐭𝐞𝐦𝐬 (𝐈𝐃𝐒): Deploying software and hardware solutions to monitor and control network traffic, identifying and blocking suspicious activities.
𝐕𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐲 𝐌𝐚𝐧𝐚𝐠𝐞𝐦𝐞𝐧𝐭: Regularly scanning systems for vulnerabilities and applying patches and updates to mitigate potential security risks.
𝐄𝐧𝐜𝐫𝐲𝐩𝐭𝐢𝐨𝐧: Utilizing encryption techniques to protect data both in transit and at rest, ensuring that even if intercepted, the data remains unreadable to unauthorized parties.
𝐀𝐜𝐜𝐞𝐬𝐬 𝐂𝐨𝐧𝐭𝐫𝐨𝐥: Implementing measures such as strong authentication mechanisms, access permissions, and user role management to restrict unauthorized access to systems and data.
𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐀𝐰𝐚𝐫𝐞𝐧𝐞𝐬𝐬 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠: Educating employees and users about cybersecurity best practices, potential threats, and how to recognize and respond to them.
𝐈𝐧𝐜𝐢𝐝𝐞𝐧𝐭 𝐑𝐞𝐬𝐩𝐨𝐧𝐬𝐞: Developing and practicing plans and procedures to effectively respond to and recover from cyber incidents, minimizing their impact on operations.
𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐌𝐨𝐧𝐢𝐭𝐨𝐫𝐢𝐧𝐠 𝐚𝐧𝐝 𝐀𝐧𝐚𝐥𝐲𝐭𝐢𝐜𝐬: Continuously monitoring systems and networks for signs of suspicious activity, utilizing advanced analytics and machine learning algorithms to identify potential threats.
𝐓𝐡𝐫𝐞𝐚𝐭 𝐈𝐧𝐭𝐞𝐥𝐥𝐢𝐠𝐞𝐧𝐜𝐞: Gathering and analyzing information about emerging cyber threats, attackers’ tactics, techniques, and procedures (TTPs), and incorporating this intelligence into defensive strategies.
𝐏𝐡𝐲𝐬𝐢𝐜𝐚𝐥 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲: Protecting physical infrastructure, such as data centers and server rooms, from unauthorized access, theft, and damage.
𝐑𝐞𝐠𝐮𝐥𝐚𝐭𝐨𝐫𝐲 𝐂𝐨𝐦𝐩𝐥𝐢𝐚𝐧𝐜𝐞: Ensuring compliance with relevant laws, regulations, and industry standards pertaining to cybersecurity, such as GDPR, HIPAA, or PCI DSS.